Spearphishing
Block targeted email attacks to prevent data breaches and credential theft.
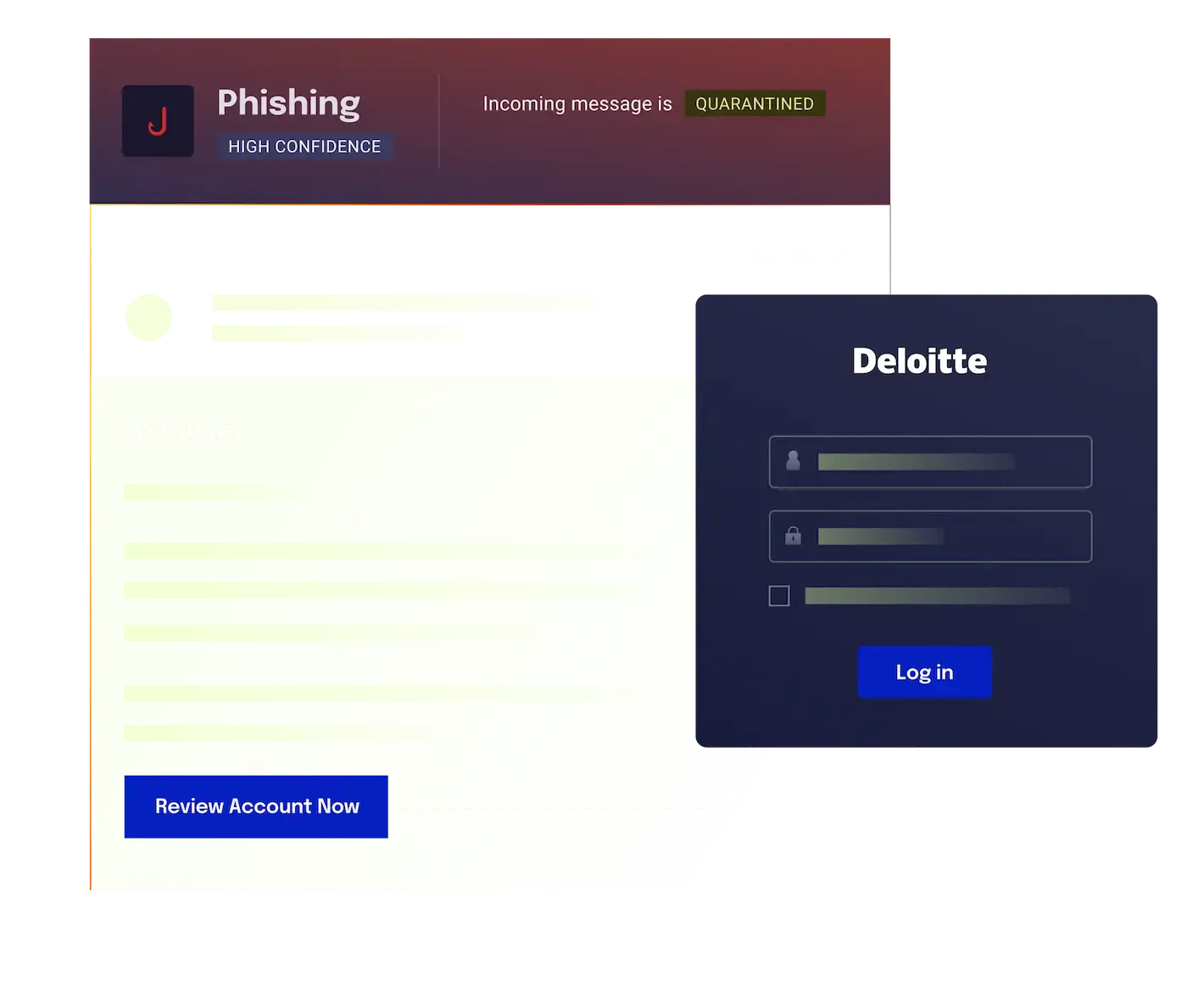
Low-volume attacks tailored to the victim
Spearphishing is a highly targeted form of phishing where attackers gather detailed information about individuals or organizations to create convincing emails. These low-volume attacks bypass traditional security by avoiding known malicious links or attachments and exploit trust in familiar brands and partners.
Victims are tricked into revealing sensitive data or granting unauthorized access to internal systems. Spearphishing often serves as an entry point for more serious attacks, such as account takeovers or ransomware.
How xorlab detects and blocks spearphishing
xorlab's email security uses behavioral AI to detect and block spearphishing attacks before they reach your employees' inboxes, even from compromised accounts or with personalized messaging. The solution understands your organization’s communication patterns and flags emails that deviate from expected behavior.
By analyzing email content and context, xorlab ensures that messages align with normal business operations, providing early detection of targeted spearphishing attempts and preventing harmful actions.
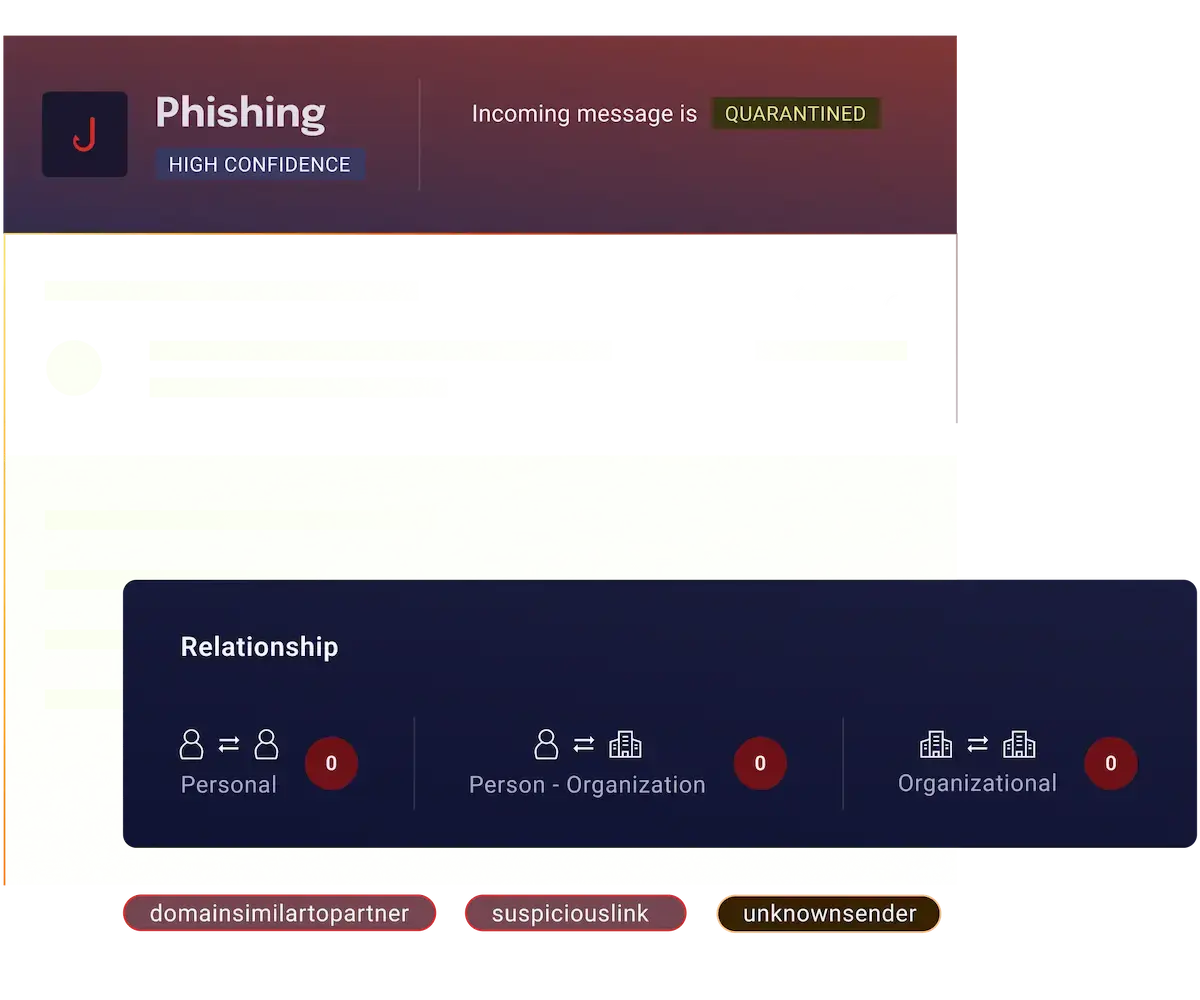
Spearphishing techniques and characteristics
Personalization
Spearphishing emails are convincing as they include personal details like names or roles.
Trust Exploitation
Attackers impersonate trusted contacts to trick victims into engaging with the email.
Emotional Manipulation
Spearphishing exploits fear, urgency, or curiosity to prompt quick responses.
Evasion
Constructed but convincing links or attachments bypass traditional defenses.
Compromised Accounts
Attackers use compromised accounts to make emails appear more legitimate.
Low Volume
Spearphishing targets specific individuals. By nature, most attacks are unique.
Within the MITRE ATT&CK® Matrix, spearphishing maps to Phishing for Information and Phishing as two techniques (and their sub-techniques) aimed at the tactical objective of Reconnaissance and Initial Access.
Resource center
Ciso Guide
Explore our ebook about smarter email security – an attacker-centric, proactive approach.
Attack simulation
Stress test your email security with our realistic email attack simulation.
Pen-test your email security
False negatives causing extra work? Unsure of your protection against spearphishing attacks? Identify gaps with xorlab's Email Attack Simulation.
Trusted by organizations with highest security needs

















