QR code phishing
Detect malicious emails with phishing links in images like QR codes.
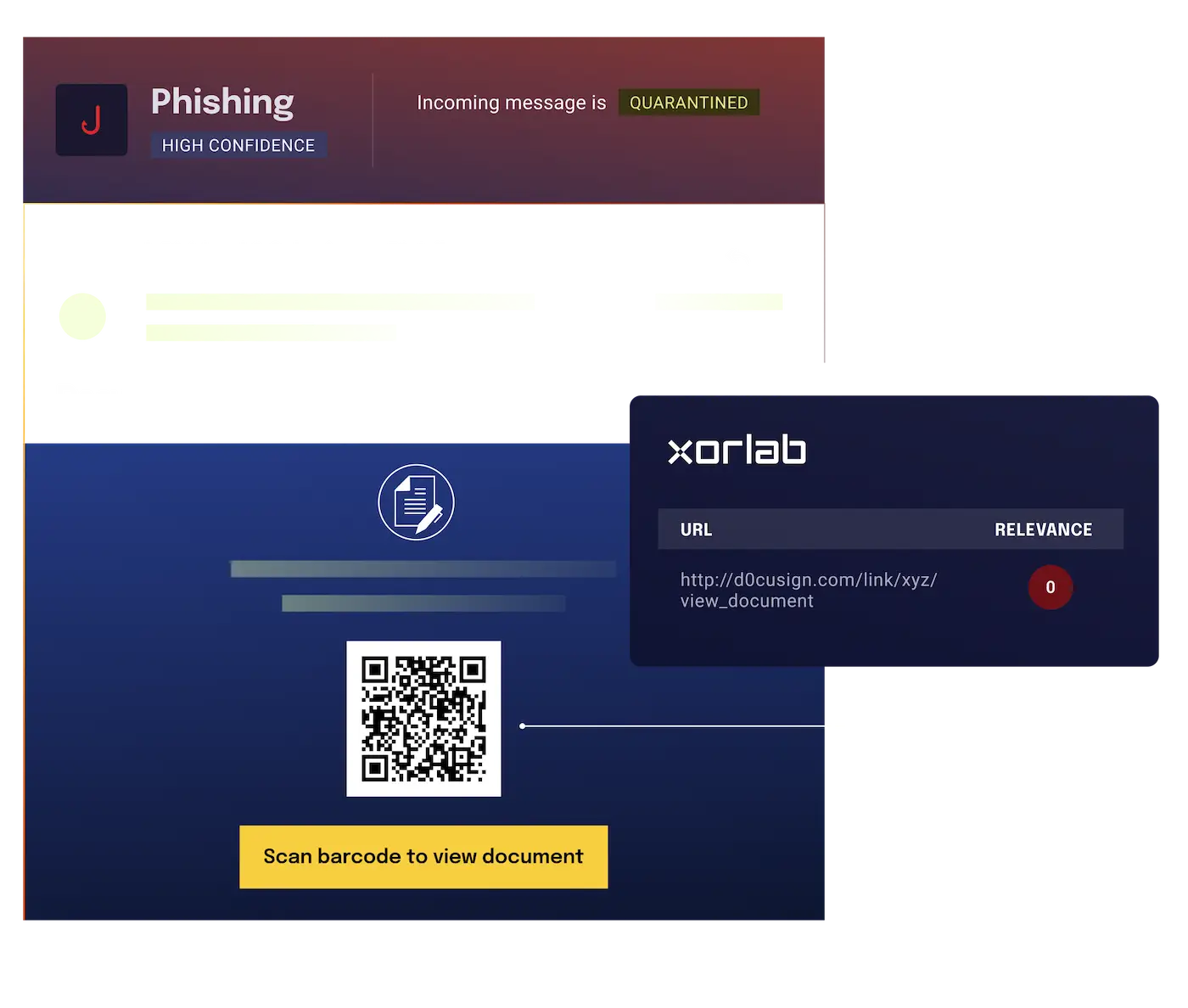
Attackers evade link detection with QR codes
Links embedded in QR codes often evade link detection and subsequent security analysis. Further complicating detection, QR code attacks impersonate trusted brands, vendors, or internal communications, making it difficult for users and traditional email security to identify the threat.
Once scanned, the QR code directs the victim to a fraudulent website that mimics legitimate services, aiming to steal credentials or install malware.
Similar to credential phishing, QR code phishing (quishing) can target specific high-value individuals, like executives or finance staff, or be part of mass campaigns.

How xorlab detects and blocks QR code phishing
xorlab analyzes images in emails and attachments and uses QR code analysis to identify the type of data stored within the QR code. The solution extracts QR code encoded links and evaluates the relevance of the linked content in the context of the sender-recipient relationship.

QR code phishing techniques and characteristics
Impersonation
Attackers leverage trusted brands or hijacked email threads to embed QR codes into seemingly legitimate conversations.
Evasion
Malicious URLs are hidden within QR codes, making traditional email security measures less effective at detecting the threat.
Urgency
Quishing emails often contain urgent calls to action, pressuring users into acting quickly.
Obfuscation
The malicious URL is masked by redirects, preventing victims from easily identifying the phishing site.
Device Targeting
QR codes are designed for mobile devices, which are more vulnerable to phishing attacks due to smaller screens and less stringent security measures.
Embedding
QR codes can be embedded in files like PDF or Office file formats making it even harder to detect for traditional email security solutions.
Within the MITRE ATT&CK® Matrix, QR Code Phishing maps to Phishing for Information and Phishing as two techniques aimed at the tactical objective of Reconnaissance and Initial Access.
Resource center
Ciso Guide
Explore our ebook about smarter email security – an attacker-centric, proactive approach.
News
How attackers leverage the trust of GitHub to launch targeted phishing attacks.
Attack simulation
Stress test your email security with our realistic email attack simulation.
Pen-test your email security
False negatives causing extra work? Unsure of your protection against QR code phishing attacks? Identify gaps with xorlab's Email Attack Simulation.
Trusted by organizations with highest security needs

















