Put your email security to the test
See what’s happening in your email security and close critical gaps fast with the industry’s largest collection of real-world attack techniques — no allow-lists required.
Trusted by organizations with highest security needs


















Why test your email defenses with realistic attacks?
Discover weaknesses as early as possible and before attackers do.
Complement penetration tests as they often overlook email.
Assess your email security posture with the full range of email attacks.
Simple and easy email penetration test
xorlab's attack simulation tests your defenses against modern email threats. Choose the attack types to test and get actionable insights to reduce your attack surface – all within one week.
Scenarios
Tailor attack types, methods, and obfuscation tactics to your needs.
Simulation
Receive realistic attacks from xorlab to the designated inbox.
Data export
Submit a PST export of that email inbox and xorlab analyzes the data.
Results
Get results and recommendations – identify gaps within one week.
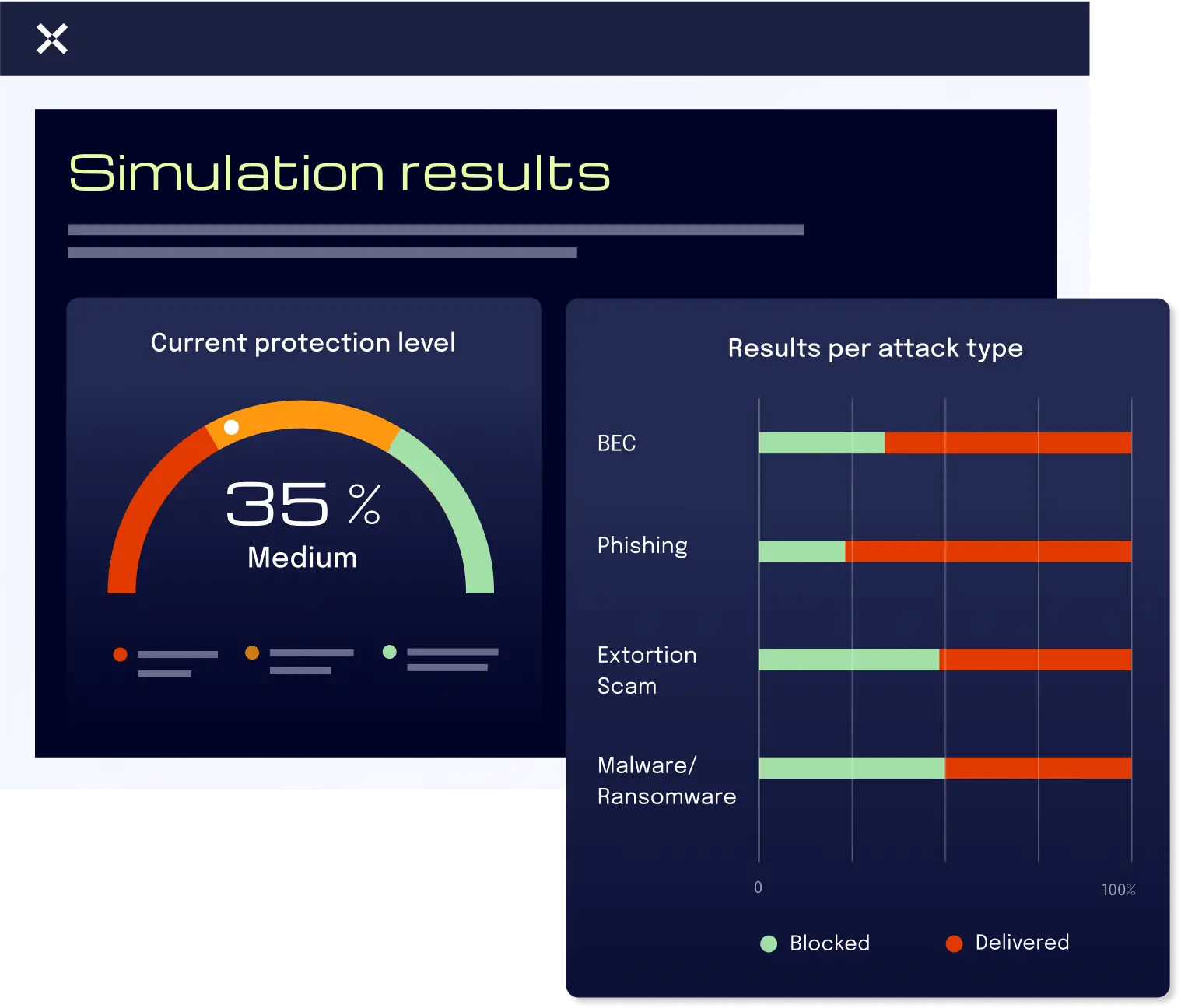
Quick results, clear insights
The simulation report offers a detailed assessment of which attack types were detected and which bypassed your current solution.
You will receive tailored recommendations for closing any security gaps.
Discover how xorlab stops modern email attacks
Frequently Asked Questions
What do I need to do?
Nothing – sit back and relax! Once the details have been clarified and you have given us a recipient address, xorlab will start the simulation.
How much effort will the attack simulation require of me?
On average we ask for about 2 hours of your time: For the kick-off meeting, providing a designated mailbox, sending us the PST file export, and attending the meeting where we present the results - that's it!
Do I need to whitelist domains?
No, you don't. As our goal is to test your infrastructure end-to-end, you do not need to whitelist any domains.
How soon can we start with the simulation?
We will contact you after receiving the request. The only task before getting started with the simulation is for you to choose the scenarios. As soon as these are chosen, we can get started.
Which attack types, methods and obfuscation tactics are part of the simulation?
We discuss your organization's needs and choose from the following:
Attack types: Business email compromise, credential phishing, spearphishing, QR code phishing, malware, and more.
Attack methods: Spoofing, lokalike domain, open redirect, VIP impersonation, brand impersonation, PDF files, Office macros, and more.
Obfuscation tactics: HTML smuggling, QR code, URL shorteners, content as image, and more.
Will any of my data be exposed during the xorlab attack simulation?
No, we will only simulate realistic attacks. Your company will not be exposed to real phishing, malware or anything else that could harm your systems.