Top 5 Microsoft 365 email security concerns
Microsoft leads the cloud-based productivity software market with its Microsoft 365 suite. The popularity of M365 (formerly known as Office 365) exploded in 2020 and 2021, as organizations worldwide were forced into remote work due to the pandemic.

Recent data by Statista shows that now over a million companies worldwide use Microsoft 365 to facilitate collaboration, improve productivity, and meet their communications needs.
With organizations moving towards M365 at unprecedented speeds, many decision-makers may not be aware of all the security aspects that need to be considered before making the move. Email security specifically is still a problem for many organizations, and security leaders should use the switch to M365 as an opportunity to look beyond what the software giant from Redmond has to offer.
The New Challenge Facing Security Teams
Email is the most widely used business application and the number one vector of cyberattacks. 9 out of 10 attacks against businesses start with a malicious email and 75% of ransomware attacks are email-borne.
Today, email attacks are harder to detect than compared to a couple of years ago. Cybercriminals have moved beyond mass phishing and trivial malspam campaigns to leveraging mass-personalization and evasion techniques and continue to deliver their attacks to employee mailboxes. As the volume and sophistication of these attacks increase, corporate defenders struggle to keep corporate inboxes free from email lures.
With many security filters missing features to dynamically control the attack surface and only providing static parameter-based configuration, many defenders are forced to implement harsher policies at the cost of increased organizational friction and cost. If they don’t, they actually expose their organizations to more, unnecessary risk.
Many attributes, such as sender IP or URL patterns that not long ago could be used to fully identify an attack across a broad spectrum of victims, now change within a single campaign against one victim. Security teams not only need to prevent attacks that they have no knowledge about today, but they also need to constantly evolve and adjust their defenses to protect against tomorrow’s attacks.
While Microsoft 365 includes a number of useful capabilities to defend against today’s broad range of email-borne threats, even its highest tier, Microsoft Defender for Office 365 Plan 2, still has some blind spots and it is important for organizations to be aware of them and take adequate measures.
Overview of Native M365 Security Controls
Microsoft provides three levels of native security services: Exchange Online Protection (EOP), Microsoft Defender for Office 365 Plan 1 (Defender for Office P1), and Microsoft Defender for Office 365 Plan 2 (Defender for Office P2). EOP is the default for all subscriptions, while Defender for Office P1 is included in Microsoft 365 Business Premium and Defender for Office P2 comes with E5. Organizations can also choose to add Defender for Office P1 or P2 as an add-on to certain subscriptions.
The three levels aim at different use cases (from the documentation):
- EOP: Prevent broad, volume-based, known attacks.
- Defender for Office P1: Protect email and collaboration from zero-day malware, phish, and business email compromise.
- Defender for Office P2: Add post-breach investigation, hunting, and response, as well as automation and simulation (for training).
While EOP might be enough for dealing with broad, volume-based spam, malware, conventional phishing attacks, it only offers a basic level of email security. Security leaders deciding on a single-vendor strategy should at least put their organization on Defender for Office P1. And if they want to be able to respond to active threats, a P2 subscription is encouraged.
Any company’s defense system should include a strong filter that can identify and stop a significant amount of fraudulent email – which serve as the initial entry point for malware and ransomware extortion attacks, business email compromise, and fraud – long before they can become a problem for the organization. To have the best chance of defending their organization against new and targeted email threats, security leaders should carefully evaluate whether the tools provided by Microsoft are adequate for such needs. Before making a purchase, they should first understand the gaps within M365.
Microsoft 365 Email Security Concerns
#1: Phishing Defense Is Full of Gaps
In terms of phishing defense capabilities, Microsoft Defender seems to not keep up with customer expectations. A 2020 Osterman Research white paper notes that obvious spam and phishing attacks still bypass Defender’s detection and are eventually delivered to user mailboxes. This limitation should not be underestimated. When it takes just one user to fall for a phishing email and trigger a serious incident, delivering high catch rates is a critical aspect to look for in an email security solution.
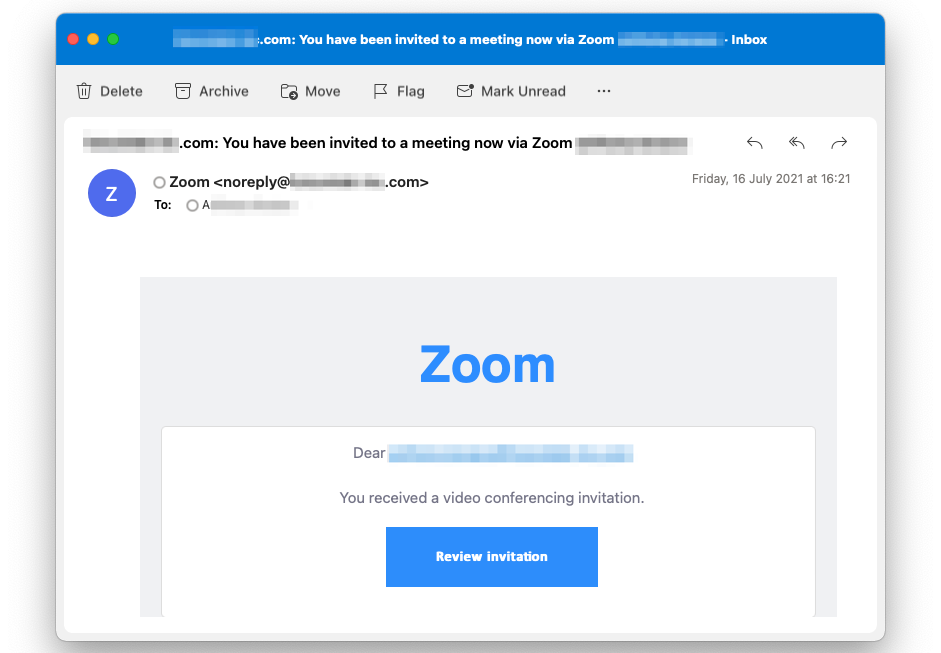
Anonymized screenshot of a fraudulent Zoom meeting invitation. xorlab received reports from M365 customers who could not stop an entire wave of Zoom-themed phishing attacks despite using Office 365 Advanced Threat Protection (now Microsoft Defender for Office 365) at that time. (Source: xorlab.com, 17.02.2022)
Such false negatives (malicious emails that bypass the email security solution) are usually caused by the fact that the security filter could not produce any malicious markers when inspecting the fraudulent email, and therefore had to deliver. Malicious markers can be anything from known bad senders, malware signatures, and known URLs to “machine-learned” metrics such as similarity to phishing emails observed in the past. But bad actors have become really good at hiding these markers and bypassing initial filtering by weaponizing content after delivery.
#2: Targeted Attacks Can Bypass ZAP
With Zero-hour auto purge (ZAP), Microsoft aims to remedy the false negative issue by retroactively detecting and neutralizing malicious phishing, spam, or malware messages after delivery. ZAP could be a good solution to quickly identify any delivered email threats, but only if it covered more scenarios.
The scope of ZAP is limited to mailboxes on Exchange Online. Customers running hybrid setups cannot fully benefit from ZAP, and it also only works under a limited set of conditions:
- Detection needs to happen within 48 hours after delivery. If a threat stays below the radar for longer, ZAP won’t be able to neutralize it.
- ZAP continually monitors updates to the malicious markers database and automatically removes from users‘ mailboxes messages that produce a match. By definition, ZAP cannot help Patient Zero victims.
Attackers who keep the volume of their campaigns low, target recipients in a single organization, and use untainted phishing sites or malware files have a high chance of keeping their threats off the ZAP radar.
#3: Safe Links Only in Office Documents
Another shortfall lies with Defender’s Safe Links feature. Safe Links scans URLs, rewrites inbound email messages in mail flow, and provides time-of-click verification of URLs and links in email messages and other locations. However, the coverage of Safe Links is limited to email messages and Office documents. Organizations won’t be protected against attacks that hide malicious URLs in PDF files and other non-Microsoft documents.
What’s more, if Safe Links cannot identify the link as malicious at the time of click – which is unlikely to happen with targeted, low-volume attacks – it will not prevent the recipient from visiting the site. As a result, users might still land on a phishing site and become compromised.
#4: Limited Visibility and Control
Attacks will undoubtedly increase in sophistication and will put pressure on teams to configure, manage and update security filters as efficiently as possible. Fast-moving security teams may quickly realize that teaching new tricks to Defender is harder than it should be. Filter policies are essentially a collection of switches and flags that can be turned on or off.
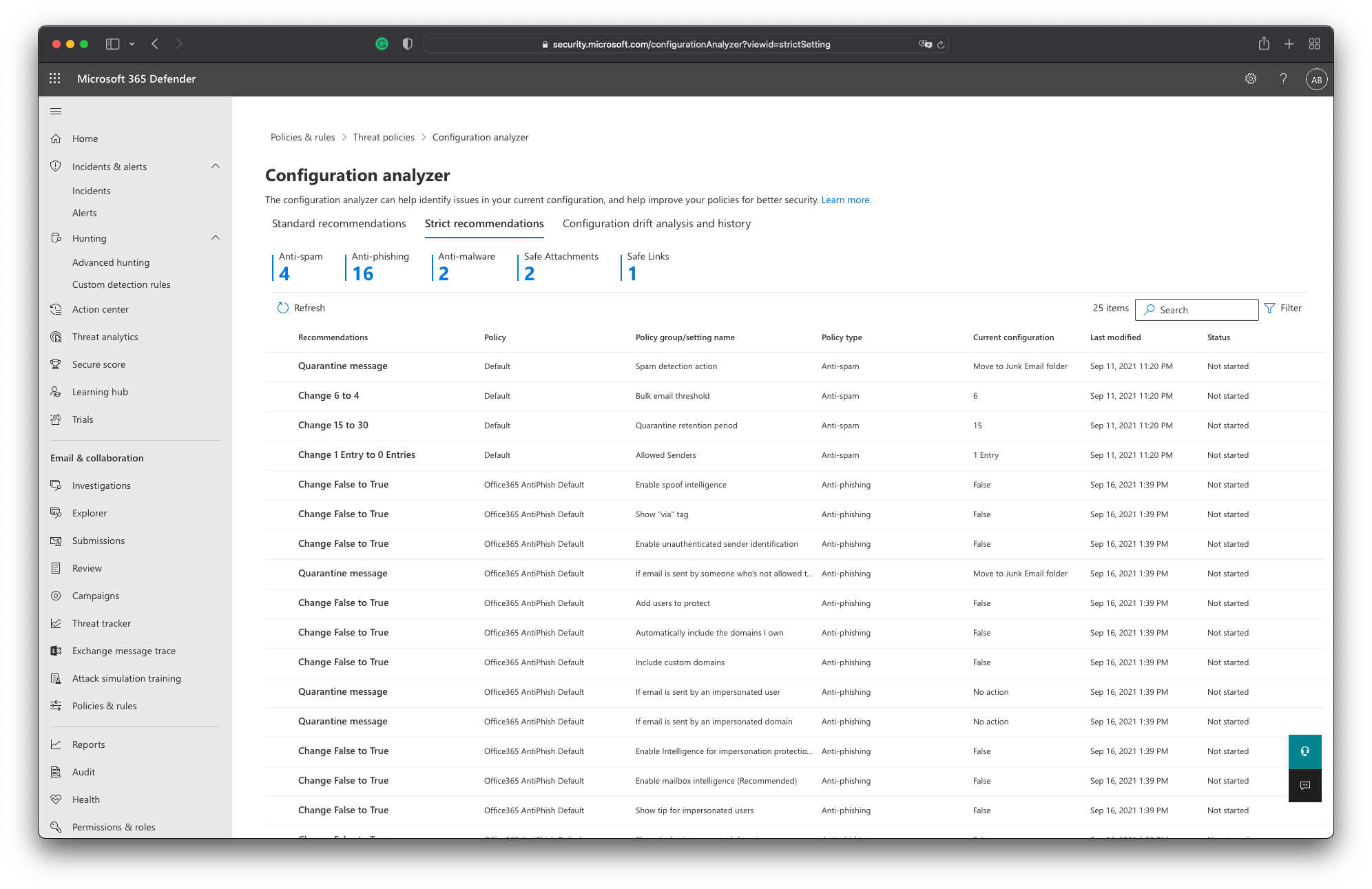
The configuration analyzer in Microsoft 365 Defender provides an overview of the possibilities to tune policies and recommends best-practice settings. (Source: docs.microsoft.com/en-us/microsoft-365/security/office-365-security/overview?view=o365-worldwide, 17.02.2022)
Defender is a black box whose internals remain in the control of Microsoft. Security operators don’t have the means to customize and tailor the controls to their individual needs. They can report issues back but there is no feedback. Even though Defender provides some level of background information about its decision, this information is usually not enough to build an understanding about and devise changes.
#5: Inefficient User Interface
When it comes to confirming and prioritizing detected email threats, security professionals struggle to maintain an integrated view. Defender’s user interface (UI) does not provide all the information on a single screen, meaning that analysts have to spend time collecting the information required to confirm and prioritize threats.
Another UI limitation concerns the sorting and prioritizing of threats by severity. Defender does not expose scores on the UI, and the real-time detections report (available with Defender for Office P1) only discriminates between emails that were identified as malicious due to phishing or malware. Viewing a list of all emails is only possible with Threat Explorer in Defender for Office P2.
How to Boost M365 Built-In Defenses
With over a million companies using M365 currently, it is crucial that security leaders understand the limitations of its native security capabilities and take appropriate measures to cope with today’s threats. Microsoft does provide a broad set of tools that promise to ensure sufficient email protection – and adopting a single-vendor approach may have its benefits – but not all the capabilities in M365 will meet the requirements of every organization.
If their organization relies on M365, teams will need to complement security with proven and dedicated solutions from third-party vendors.
Conclusion
In the quest to help organizations stay one step ahead of threat actors, AI-enabled, machine learning solutions could provide the necessary capabilities. Such solutions continually analyze, adapt, and evolve based on the risk profile of every email they process. They understand the context of communications and leverage this knowledge to detect anomalies and stop threats unique to an organization.
This post was originally published on Tec-Bite (24.2.2022).
Want to learn more about email security? Download our free Email Security Guide or Book a Demo.

