Why today’s email security must be adaptive and AI-based
The evolving email threat landscape Email remains the most common attack vector for cybercriminals, but the nature of these attacks has fundamentally...
Business Email Compromise (BEC) is an attack in which the bad actor delivers phishing, fraud, or malware via a previously compromised, legitimate user account. BEC attacks typically originate from well-known suppliers and other business partners and use a sophisticated series of steps to ultimately trick the victim into providing valuable information or moving money directly into the attacker’s bank account.

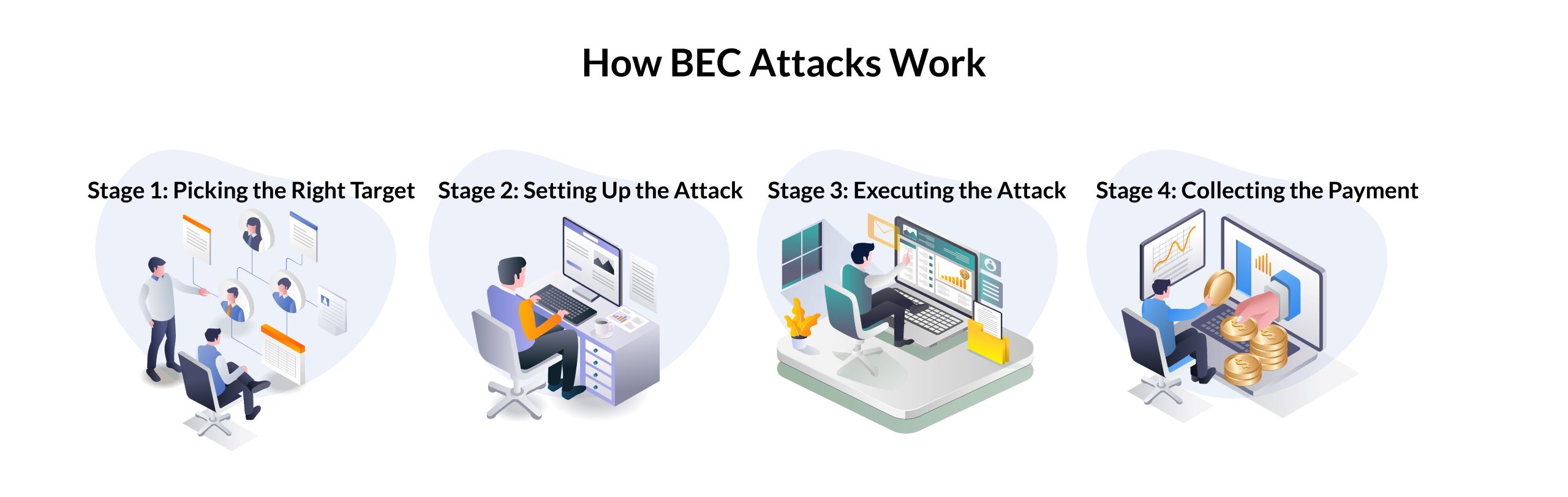
According to the FBI, Business Email Compromise alone accounted for nearly 35% of all cybercrime losses in 2021, and that number is only growing as threat actors become more effective. Cybercriminals are constantly innovating, launching new attack tools and technologies to get through traditional cybersecurity defenses such as signature-based gateways and into the accounts that are most valuable to them. They use advanced social engineering tactics and techniques, including spear phishing, to gain access to corporate email accounts and send fraudulent emails to steal money from the target company.
Over the past few decades, email security solutions have looked to mitigate email risk by preventing previously seen attacks from occurring again. Mail server reputations, fast sharing of intel and signatures, URL rewriting, dynamic analysis of files and URLs—many approaches have been developed to cope with the changing nature of email threats. But these approaches inevitably result in playing catch-up with bad actors. Legacy security tools reliant on signatures and threat feeds are ill-equipped to tackle the new age of rapidly evolving cyber threats.
Modern email attacks like BEC are highly personalized, exploit trusted relationships (Fig. 1), and use untainted senders and infrastructure. Attackers dynamically create “fresh” malicious links and unmarked attachments, which render the previously strong indicators obsolete. As a result, more and more malicious emails reach your employees' inboxes where they increase the risk of breach, overhead, and friction.

Fig 1. BEC involves an attacker abusing a compromised, legitimate email account to send malicious messages. In this example, the allegedly compromised sender’s email address might be placed in the display name creating the impression that it was the actual business partner who sent the email.
How to respond when the email attack surface is dynamic and threat actors are relentless in their onslaught against it? A constantly evolving cyber-attack landscape requires a step up in your detection capability.
Context Intelligence can help you regain the upper hand. Completely independent of third-party threat intelligence, Context Intelligence brings together data and signals from different internal and external sources, giving you the visibility you need to understand and adapt the attack surface to the dynamic needs of your organization. Without context:
With Context Intelligence, you will finally be able to understand and minimize your attack surface, identify modern threats more accurately, and detect anomalies in trusted communication. Here's how you can start.
When you get visibility into and understand what legitimate communication looks like for your organization, you can understand your unique environment, filter the noise, and take action where potential risks are identified.
To find out more about how you can apply Context Intelligence to protect your organization against BEC and zero-day email attacks, check out The CISO Guide to Smarter Email Security.
The evolving email threat landscape Email remains the most common attack vector for cybercriminals, but the nature of these attacks has fundamentally...
 xorlab team
xorlab team
How email bombing works Email bombing involves overwhelming a target’s inbox with an excessive number of email messages in a very short time. The...
 Threat Analysis team
Threat Analysis team