Phishing Gets Personal

With more than 80% of reported incidents[1] starting with a phishing email, phishing is the most common cause of data breach and a big risk to organizations. According to a study by Verizon, a whopping 30% of phishing emails are opened by users and 12% of those who open click on the malicious link[2]. Considering the relatively low effort attackers have to put into successful campaigns, phishing is a lucrative business for cybercriminals.
Phishing emails are not new but they (still) work. In fact, they work better than ever looking at the rising number of successful phishing campaigns. As a result, companies are heavily investing into security awareness programs to equip their staff with the skills to spot any attack lingering in their mailboxes. This led to criminals increasing the level of sophistication of their campaigns, which makes them more difficult to spot. And so, the game of cat-and-mouse continues. With the current level of phishing craftmanship, chances are high that one day even a trained employee in your organization will mistake a forfeit email for a legitimate one. The consequences of one such a mistaken click can range from financial and reputational loss to a full-fledged ransomware attack.
What is phishing exactly?
Put simply, phishing is credential theft, taking place with the active assistance of the unwary victim. Phishing is a type of cyberattack that uses a disguised email (or any other medium) to trick the user into revealing personal data – most often account credentials such as usernames and passwords. The attackers, often under the pretext of resetting a password or settling an outstanding payment, seek to create a sense of urgency, curiosity or fear which prompts the user to click on the malicious link. The victims, in the belief of dealing with a legitimate party, click on the link leading them to a malicious website. The deceptive website is designed to closely mimic a legitimate service and its login pages contain credential-harvesting scripts.
Although phishing is possible via text and voice messages (referred to as Smishing), the most common means of phishing is via email and attackers like to impersonate business partners or well-known brands such as Microsoft, LinkedIn, Amazon, Zoom to maximize conversion and lure individuals to leak their data. Phishing is deception: Both the phishing email and the counterfeit website are nearly identical in their appearances to their legitimate versions – at least at first sight.
The main types of phishing
At its core, phishing is a form of social engineering, a type of attack that involves psychological manipulation to fool victims into giving away confidential data. Phishing campaigns greatly vary in their level of personalization, moving on a broad spectrum between mass campaigns and very targeted, carefully crafted, and tailored attacks.
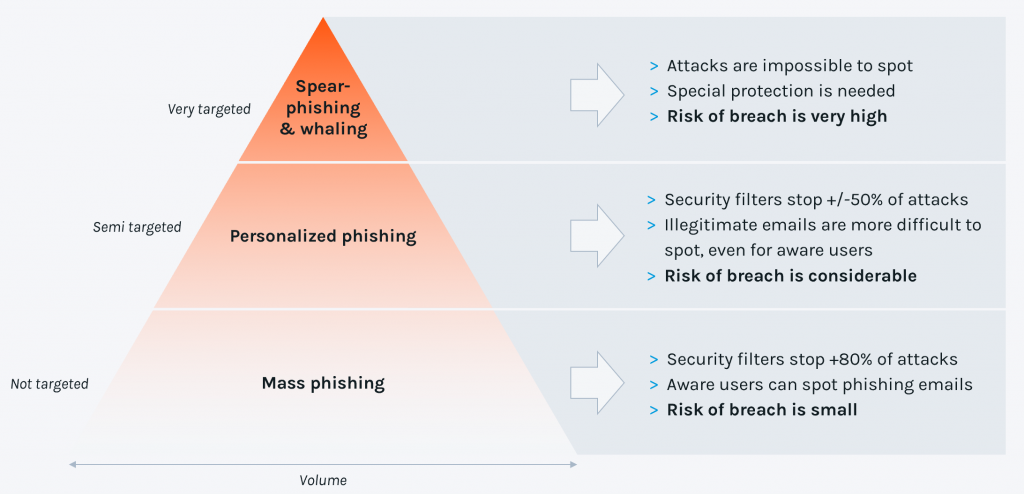
At the lower end of the spectrum is mass or bulk phishing. These emails use the “spray and pray” technique; they are general and are being sent to random users and to as many addressees as possible. Bulk phishing messages are usually easily identified and deleted by users, but there will always be employees prone to falling for them. Security awareness trainings and phishing simulations are therefore important. From the technical perspective, the risk of mass-phishing can be mitigated easily if the filters in place are regularly updated and have the most recent IOC available.
Personalized (or semi-targeted) phishing is more customized hence more dangerous. Attackers put an effort into personalizing their messages to target particular individuals, often referring to them by their names. These campaigns target particular industries or geographical regions. Personalized phishing attacks are more difficult to spot and prevent than bulk phishing campaigns and neither employees, nor traditional filtering solutions can stop them with high certainty. Accordingly, the risk of credential theft is considerable. Also important to mention is that attackers are able to personalize campaigns at scale, which further increases the risk of breach.
Spear-phishing is highly targeted and poses a very serious risk to any organization. Spear-phishing emails contain personalized information about the target, use a more elaborate writing style and a tone and context with which the victim is familiar. These emails are carefully crafted and are hard to spot for the user. Spear-phishing attacks are low volume and fresh, which lets them easily evade traditional detection systems.
Whaling is a subtype of spear-phishing targeting the “big fish” in an organization, typically senior executives and other high-profile targets. A great deal of effort and research goes into tailoring the message to the victim. Attackers study the victim and his/her network. Whaling emails often impersonate known contacts or use a language style that is characteristic of the victim’s contacts. These emails appear as highly credible, are extremely difficult to spot and can only be thwarted by the most advanced defense controls.
How to spot phishing emails?
What all types of phishing emails have in common is that they demand some form of action – usually urgent – from the recipient. However, just as the level of personalization varies for the different types of phishing emails, so does the number of telltale signs, indicating to the user that s/he might be dealing with a phishing email. For example, in case of bulk or targeted phishing, there are several signs pointing into the direction that the email is not legitimate. The following clues should make you suspicious:
- Sender email address spelling
- General or impersonal salutation such as “Dear Customer”
- Weird or even bad linguistic style
- Missing context
- Spelling mistakes, bad grammar, both in the subject and in the body of the mail
- Suspicious link, eventually containing spelling mistakes
- Inconsistencies in email addresses, links, and domain names.
These signs are a pretty good benchmark for detecting less personalized illegitimate emails, however, in case of spear-phishing and whaling, they are no longer enough to protect your organization against phishing attacks. These types of highly targeted emails are almost impossible to detect for humans and traditional email filtering solutions alike. As phishing emails are becoming more sophisticated, relying solely on the above criteria (and most importantly, on your employees) will result in a breach eventually.
Why is phishing getting more dangerous?
Phishing emails are not only getting more sophisticated, but also grow in numbers. The number of phishing attacks observed by the Ant-Phishing Working Group[3] and its members grew through 2020, doubling over the course of the year.
Phishing is a lucrative business to attackers, because phishing emails are effective and campaigns can be created with little investment. Email users are experiencing information overload, making them less attentive to spotting phishing attempts and increasing the likelihood of a click. Phishing kits – the tools to create phishing emails and matching counterfeit websites – are becoming low-cost and designed to help amateurs with little IT knowledge to get into cybercrime, increasing the number of phishing attacks.
Phishing opens the door to more serious, devastating hacking incidents, which might cost an organization not only serious money, but its reputation as well. For example, once having access to an employee’s account, attackers can use this account to move laterally within the organization and deliver targeted phishing attacks to higher-value targets.
Social engineering attacks rely on human error rather than vulnerabilities in software and operating systems. Mistakes made by legitimate users are much harder to identify and thwart than, say, a malware-based intrusion. While awareness training has its merits and good security culture is a very important and an integral part of an organization’s cyber defense, simply making your employees aware of suspicious emails is often not enough.
How can I protect my organization against phishing attacks?
With overloaded users and low entry costs for social engineering attacks, phishing poses an underestimated, yet serious threat to any organization. Modern cyber defense solutions and an engaging security culture can mitigate the risks.
Classical and cheap mass phishing campaigns are easily detectable by traditional security filters and can be blocked most of the time. Personalized phishing attacks, spear-phishing and whaling are much more difficult to catch – by the recipient and by traditional filtering solutions. These require novel methods that do not rely on IOC sharing, IP and sender blocklists, and URL blacklists.
Currently available and effective protection methods use machine learning (ML) and artificial intelligence (AI) to detect attacks at first sight. The freshness and targetedness of today’s phishing attacks make it imperative to detect and stop attacks without having to rely on information from past attacks because this information simply does not exist. Every attack has to be treated as a new attack and your defense controls must cope with that.
Phishing protection from xorlab
xorlab's ActiveGuard platform and its contextual threat detection engine understands local context, relationships, and communication behavior. xorlab’s software leverages insights from your organization’s communication history to spot and stop, at first sight, advanced phishing, business email compromise (BEC), and ransomware attacks.
With phishing getting more personalized and more targeted, deploying a system such as ActiveGuard lets you personalize your defense and fight targeted attacks more effectively. The benefits are not only reducing your risk of breach but at the same time minimizing the number of false positives.
If you’d like to learn more, drop us a note and we will be happy to get in touch with you.
[1] https://www.varonis.com/blog/cybersecurity-statistics/
[2] https://www.verizon.com/about/news/verizons-2016-data-breach-investigations-report-finds-cybercriminals-are-exploiting-human

