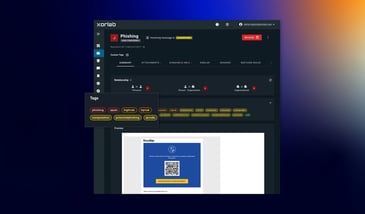
Open Redirect Vulnerabilities: The Hidden Danger in Email Security
In this article, we explore how open redirects, a vulnerability in web applications, are leveraged...
7 min read